IDcypher Hash Functions .NETIDcypher Hash Functions .NET
IDcypher is a security-related component library, which lets you incorporate strong encryption into your application.IDcypher Hash Functions .NET
IDcypher is a security-related component library, which lets you incorporate strong encryption i...
Overview
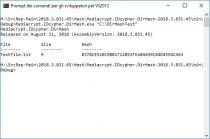
Mediacrypt IDcypher Component v2018.3.831
(For .NET 4.x) released on August 31, 2018
(IDcypherFull.dll, Dynamic Link Library, DLL)
==========
Mediacrypt Customer Support
==========
Revision History:
2018.09.01 (September 01, 2018):
- ADDED: IDcypher.DirHash-2018.3.831.45 (User Interface, UI);
2018.08.31 (August 31, 2018):
- ADDED: IDcypher.StringHash-2018.3.831.45 (User Interface, UI);
- ADDED: IDcypher.FileHash-2018.3.831.45 (User Interface, UI).
==========
Examples:
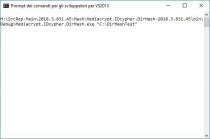
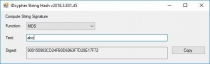
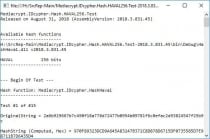
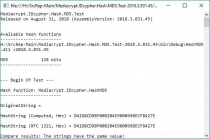
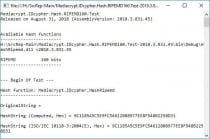
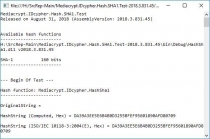
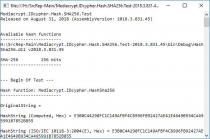
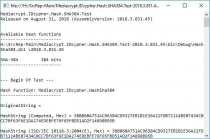
- IDcypher.Hash.MD5.Test, Provider: MD5 (Console output);
- IDcypher.Hash.SHA1.Test, Provider: SHA1 (Console output);
- IDcypher.Hash.SHA256.Test, Provider: SHA256 (Console output);
- IDcypher.Hash.SHA384.Test, Provider: SHA384 (Console output);
- IDcypher.Hash.SHA512.Test, Provider: SHA512 (Console output);
- IDcypher.Hash.RIPEMD160.Test, Provider: RIPEMD160 (Console output);
- IDcypher.Hash.HAVAL256.Test, Provider: HAVAL256 (Console output).
- IDcypher.DirHash, Provider: SHA1 (Console output);
==========
IDcypher is a security-related component library, which lets you quickly and easily incorporate strong encryption into your application.
The three pillars of Information Security:
Confidentiality: protecting information from unauthorised disclosure;
Integrity: protecting information from unauthorised modifications, and ensure that information is accurate and complete;
Availability: ensuring information is available when needed.
==========
Developers are able to create spectacularly powerful applications, which transform everyday life for individuals, but when a company's assets or reputation are on the line the stakes become much higher. In the information age and in the interdependent digital economy that is driving globalization and progress today, protecting a company’s sensitive files in any way possible is the key to survival. There are competitors who are willing to try almost any means to get at your data, and one of the most damaging breaches that a company can suffer is that of intellectual property that has been painstakingly developed and perfected being appropriated or misused at the hands of a competitor.
Intellectual property is under siege through the actions of hackers who are able to access systems remotely and with relative immunity to repercussion. The victims of this crime often do not get redress. Financial systems are particularly sensitive to being hacked because of the large amounts of very valuable data that they process. For a corporation, the compromising of intellectual property to a significant enough degree could carry a price tag in the millions. Developers must arm themselves against the various forces that are working against them. Cryptographic methods have been long utilized to protect business. But technology can also be used against an enterprise. IDcypher is designed to combat this threat.
Mediacrypt.IDcypher is a newly developed security library, which is now available to the general developer community. Containing an array of powerful tools, hash functions, and ciphers, IDcypher is designed to bring a complete package of encryption and security aids easily to hand. Data compression and encryption are accomplished with platform-independent code that will work in 32 bit and 64 bit environments. Advanced features such as Encrypted Storage provide reliable protection for structured and file-based data.
Standard .NET classes are used as a template for library components. This serves the dual purposes not only of adding encryption features to newly developed programs, but additionally it makes the refactoring of encryption to existing programs a far more streamlined process. Basic and multi-threaded ciphers can be loaded into the IDcypher library side by side, and are automatically accessed by the system, which is using the library. The ability of IDcypher to load compatible components transparently makes easy customization to the target environment possible simply by copying the required component set. IDcypher can then adapt on the fly to the target operating system, number of cores, hardware configuration, and so on.
IDcypher includes a unique Key Manager component, which will transparently handle user-supplied passwords and binary keys. This will save an enormous amount of time and headaches for developers otherwise forced to write code for the management of passwords and keys.
Prominent in the IDcypher toolkit is the file shredder, which securely removes data after it has been encrypted. The shredder overwrites data a given number of times, making data recovery less feasible with each pass. After the data is completely erased, the shredder deletes the file, removing every trace of its directory record. The file data is scrambled to such an extent that the original file cannot be reconstituted by any means.
With all these capabilities encapsulated in one package, IDcypher is the preeminent tool for developers today to secure important intellectual property from those who would misuse it. Applications must be secured to ensure that your business is secure. IDcypher from mediacrypt.com is your secret weapon against hackers.
IDcypher does not contain unmanaged or unsafe code; all the components are platform-independent and can be run in both 32-bit and 64-bit environments (with exception of a few optional platform-optimized components).
Mediacrypt.IDcypher Library (High Performance Multi-Threaded, Military Grade Encryption, Patent pending Key Management).
IDcypher and the IDcypher Logo are registered trademarks of Trust 47 Fund (Registration Number: 302016000012990).
==========
About mediacrypt.com (https://www.mediacrypt.com/)
mediacrypt.com, a division of the Trust 47 Fund, is an innovative independent Italian provider of tailored cyber security solutions and services to enterprises, financial institutions, government administrations, defense, and the media industry.
Cyber Security services
With the proliferation of Internet-enabled devices, cyber culture is growing more rapidly than cyber security. Everything that depends on cyberspace is potentially at risk. Private data, intellectual property, cyber infrastructure, and even military and national security can be compromised by deliberate attacks, inadvertent security lapses, and the vulnerabilities of a relatively immature, unregulated global Internet. Working hand-in-hand with member firm clients, mediacrypt.com helps organizations plan and execute an integrated cyber approach to harness the power of information networks to enhance business operations, increase mission performance, and improve customer support, without compromising security or privacy.
Our Mission
To create the leading digital experience delivery platform to empower our customers to create standout experiences for their customers – everywhere they engage.
Our Customers
Mediacrypt attracts innovative, digital disruptors with an unrelenting commitment to online strategies and standout customer experiences.
==========
- Why You Should Try Our Technical Support?
1. Get the Complete Technical Support Experience
When evaluating a product, you want to know what the real experience is of using that product, so we're offering FREE technical support with each of our product trials.
2. Professional Team of Technical Support Engineers
Our technical support engineers are trained to the highest levels of competence. If you encounter any issues with the product, or have any questions, call us or write us an email.
3. Prompt Response
There's nothing worse than having to wait around for an answer from customer support. This is why our support engineers will address the issue you reported right away.
- How to get support?
1. Help Desk
The preferred way to get help, find solution of a problem, sample of code or ask question is using our Help Desk.
Our support staff will answer your question as soon as possible.
2. E-mail
Contact e-mail of Mediacrypt Support Dept: support@mediacrypt.com.
Features
| Feature | Description |
| Ciphers | Components that encrypt and decrypt data using a secret key. |
| Compressors | Components that perform a lossless compression of a data stream. |
| Encoders | Convert binary data to a text string and vise versa. |
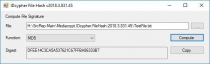
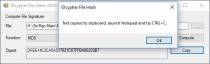
| Hash Functions | Compute a hash or a message digest of data useful for authencity/error checking. |
| Random Number Generators | Components for producing cryptographically strong sequences of random numbers. |
| Shredders | Securely destroy sensitive information. These components are required for file encryption. |
| Key Manager | Helps manage user-supplied passwords and keys. |
| Encrypted Storage | Components implementing high-level encrypted storage. |
| Documentation | Industry standard formatted help is included. |
| Royalty Free Distribution | Include with any .NET project royalty free. |
| Lifetime Support | Lifetime E-mail technical support is included. |
Requirements
- Microsoft.NET Framework 4.x;
- Visual studio 2013 – upper;
- Good knowledge of C#.
Other items by this author
| Category | Scripts & Code / C# |
| First release | 30 August 2018 |
| Last update | 3 September 2018 |
| Files included | .cs, .dll, .obj, .xml |
| Software version | .NET 4.5, .NET 4.6 |
| Tags | html, C#, css, e-commerce, visitors, encryption, tracking, SQLite, orders, sql, link, shipping, blockchain, hash, paypal payment, Active Server Page ASPX, CS, JavaScript JS, online marketplace, cybersecurity, hmac |